Table of Contents
ToggleWhat You Will Learn:
- Learn how to address the complexity of cybersecurity terminology, lengthy sales cycles, and the need for personalization in content.
- Understand the step-by-step process for aligning content with business goals, using SME insights, and targeting both decision-makers and end users.
In this guide, we will delve into the distinctiveness of cybersecurity content marketing, its significance, and various essential strategies for executing it effectively.
What Is Cybersecurity Content Marketing (+ What Makes It Special)?
Cybersecurity content marketing involves a cybersecurity firm’s strategic creation and dissemination of valuable content to engage their target audience and motivate them to take action.
So, what sets cybersecurity companies apart in their approach to content marketing?
While general content marketing principles from sources like Search Engine Journal are valuable, neglecting to address the unique characteristics of the cybersecurity audience and how to effectively connect with them can result in falling behind competitors. As a marketing agency for cybersecurity companies, we understand the uniqueness of your niche.
Here are several other aspects to consider about cybersecurity content marketing:
Keyword Complexity
Navigating intricate industry terminology in cybersecurity can pose challenges for keyword research and content creation. Often, relying on insights from thought leaders, white papers, and technical resources outside the search engine results page (SERP) is necessary to comprehensively cover specific niche topics.
Personalization
Given the diverse needs of users, cybersecurity solutions can vary significantly. Demos are frequently essential for illustrating how users can tailor an application to suit their team’s distinct requirements. Content marketing should guide users to explore further while emphasizing the importance of adapting software to meet their specific needs.
Audience
For B2B cybersecurity firms, the target audience comprises executives, business owners, and decision-makers. These individuals possess industry knowledge and seek fresh, actionable insights. It’s crucial to deliver content that resonates with their expertise, establishing credibility and trustworthiness.
Extended Sales Cycles
B2B cybersecurity companies must be prepared for lengthy sales cycles that involve engaging numerous stakeholders. In content marketing, this entails carefully nurturing leads through strategic content initiatives.

How To Build a Cybersecurity Content Marketing Strategy in 9 Steps
In cybersecurity content marketing, there is no space for taking shortcuts. Here are several strategies to position yourself for success and to stand out in a crowded b2b space.
1. Improve Your Site’s Technical SEO + UX
To ensure the success of your content, your website requires attention and care. While this holds true across all industries, it holds particular importance in cybersecurity, as virtually all current and potential customers rely on your website for information and purchases. There’s no such thing as cybersecurity window shopping.
This underscores the critical importance of technical SEO, user experience, and site architecture.
While we won’t enumerate every SEO best practice here (consult Wadi for that), we strongly advise delving deeper into impactful SEO tips through our comprehensive guide for an effective cybersecurity marketing strategy.
Technical SEO
First and foremost, your website must be exceptionally fast. Losing a prospective client due to slow loading times is simply unacceptable. Additionally, site speed now significantly influences Google’s rankings. Utilize SEO audit tools to assess your Core Web Vital scores and identify any performance issues.
Site Architecture
Consider where your content is positioned on your site. Is it structured in a manner that is intuitive for your audience(s)?
User Experience
Regarding site architecture, it’s crucial to ensure user-friendliness and ease of navigation. Having all the components in place is one aspect, but making them easily accessible and navigable is another.
For instance, if your top navigation bar is cluttered with numerous links, most of which are seldom used, it not only dilutes your link equity from an SEO perspective but also creates distractions for users.
Strive to streamline navigation on your site by incorporating elements such as breadcrumbs on every page, accessible calls-to-action (CTAs) guiding users to the next steps in their journey, carefully curated or tag-supported sections showcasing related posts at the end of each piece of content, and implementing a search function for efficient access to content hubs.
Pro Tip: Prioritize fast loading times and intuitive navigation to ensure users have a smooth experience that keeps them engaged.
2. Map Content Goals To Meet Your Cybersecurity Business Goals
Business objectives may differ among cybersecurity firms, but regardless of their nature, your content should align with and support them. For instance, if your company provides customizable premium software, your primary conversion goal might be securing a product demo. This demo can be leveraged by your sales team to establish rapport with customers and demonstrate how the software can be tailored to meet their specific needs.
Alternatively, if you offer both free and paid versions of your software, your goals may include increasing product sign-ups that eventually lead to plan upgrades through email drip campaigns. In such cases, employing a combination of top-of-the-funnel (TOFU) content to encourage free plan or newsletter sign-ups, followed by targeted messaging to encourage plan upgrades, could be effective.
3. Leverage Product SMEs and Thought Leaders for Industry Trends and Insights
To craft compelling content aimed at guiding traffic through the sales funnel, it’s crucial to have an in-depth understanding of your product.
This begins by dismantling any communication barriers between your marketing and product teams. If you have a team of Subject Matter Experts (SMEs) who have dedicated time to perfecting your software, utilize their expertise.
Engage in product demonstrations and informal interviews with members of your product team, addressing common FAQs encountered during the sales process to gain valuable insights.
This insight allows you to effectively communicate product features and use cases to your audience through your content.
When creating Bottom-of-the-Funnel (BOFU) content focused on products, consider having a senior member of the product team review the article and include them in the author byline to enhance your site’s Expertise, Authoritativeness, and Trustworthiness (E-A-T).
Furthermore, it’s essential to stay informed about industry developments. Follow thought leaders and organizations on social media, and subscribe to their newsletters for regular industry insights directly to your inbox.
You can also utilize trend analysis tools such as Exploding Topics and Google Trends to promptly identify emerging trends in your industry and capitalize on them before your competitors do.
4. Create Content for Your User Base, Not Just Your Buyer
In contrast to e-commerce, where messaging typically targets the buyer directly, B2B cybersecurity firms often require a divergent strategy. The individuals utilizing your software are seldom the ones responsible for procurement decisions. Although directing content towards decision-makers remains crucial, it’s advisable not to solely focus on this group and overlook your end users. These users are more reachable, more inclined to engage with your content, and can serve as advocates for your product among decision-makers.
Pro Tip: Create a mix of content types that cater to users at different stages of the buyer’s journey, from traffic-driving articles to conversion-focused content.
5. Choose the Right Topics and Content Types
Quality content is an investment, and it’s crucial not to squander resources on elements that don’t actively align with your overarching marketing and sales strategy. However, it’s essential to remain receptive to various content types that can bolster your strategy. Here, we’ll explore several content categories that cybersecurity companies worldwide utilize to drive traffic, sign-ups, and upgrades.
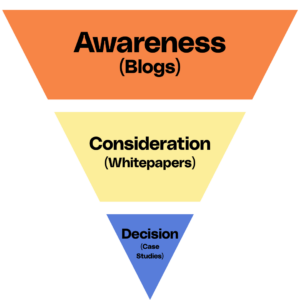
Top-of-the-Funnel (TOFU) Traffic-Driving Content:
Don’t overlook topics with substantial organic traffic and linking potential simply because they’re not directly related to your product. Examples of such content opportunities include definitional queries, “how to” guides, and “tips” listicles. Incorporating high-quality design assets into all content, especially informational TOFU content, can enhance engagement and facilitate comprehension of complex subjects. Whether it’s illustrated in-post images, infographics, photography, or styled HTML elements, these assets play a crucial role in making content digestible.
Bottom-of-the-Funnel (BOFU) Conversion-Focused Content:
BOFU content targets users who are further along in their buyer journey, leading to higher conversion rates. Common BOFU formats include buying guides, “best” roundups, “alternatives” posts, and “versus” pages. These formats provide opportunities to directly showcase your offerings, address user needs, and highlight competitive advantages.
Thought Leadership Content:
Thought leadership content enhances your Expertise, Authoritativeness, and Trustworthiness (E-A-T) while generating valuable organic backlinks. It positions your brand as an industry authority. Examples of thought leadership content include trend reports, studies, and podcasts. These formats enable you to delve into industry insights, share valuable data, and engage with your audience on a deeper level.
6.“Save” Your Cybersecurity Content With the SAVE Framework
Cybersecurity content differs significantly from lifestyle content. While adding personality and storytelling can be enjoyable, each piece of content you create should serve a purpose beyond mere entertainment.
To address this need, we’ve introduced the SAVE framework, comprising four essential qualities that every piece of cybersecurity content should embody:
- Subject-matter authority: Your content should demonstrate deep expertise, sounding like it’s authored by someone with comprehensive knowledge of the subject matter. Enhance credibility by including author bios and citations, and linking to relevant research or case studies.
- Actionability: Every piece of content should guide readers toward a clear “next step,” whether it involves downloading resources, registering for webinars, or trying out software. Readers should understand how to implement the information they’ve gained.
- Value-driven: All content should deliver tangible value to readers, making their lives easier, their work more manageable, or their organizations more secure. Address the question “What’s in it for me?” from the reader’s perspective.
- Empathy: Crafting content that resonates requires understanding your audience’s challenges, pain points, and aspirations. Incorporate empathy into your content by addressing these aspects directly.
Assess your content against the SAVE framework to ensure it meets these criteria. If any area is lacking, it’s essential to revisit and revise your approach.
7. Measure What Matters Most With the GOST Framework
When it comes to content marketing, there is a plethora of metrics available for tracking. However, not all metrics hold the same weight, particularly within the cybersecurity domain. This is why we have introduced the GOST framework – a collection of four metrics that every cybersecurity content marketer should be monitoring:
- Goals: What are your content marketing objectives, and how does each piece of content contribute to achieving them? Each content piece should align with a specific goal, whether it involves driving traffic, generating leads, or nurturing existing ones.
- Organic traffic: Although not the sole determinant of content marketing success, organic traffic serves as a crucial indicator of content performance. Monitoring organic traffic trends over time can reveal which types of content resonate most with your audience.
- Social shares: Social shares offer another valuable insight into content performance. Keeping track of the number of social shares each content piece receives allows you to identify which types of content are most popular among your audience.
- Time on page: Tracking the average time spent on each content page provides valuable insights into its engagement level. This metric helps pinpoint areas where content may need improvement to enhance engagement.
By consistently monitoring these four metrics, you can gain valuable insights into your content’s performance and make informed, data-driven decisions to refine your content marketing strategy.
Conclusion
While cybersecurity content marketing may pose specific challenges, the benefits justify the endeavor.
By comprehending your audience’s distinct requirements, establishing precise objectives, and assessing critical metrics, you can craft content that boosts traffic, cultivates leads, and facilitates the attainment of your business goals. Therefore, do not allow the intricacies of the cybersecurity domain to hinder your progress. With a suitable strategy, you can produce content that connects with your audience and delivers tangible outcomes for your business.
Key Takeaways:
- While content should engage B2B decision-makers, it’s equally important to create content that resonates with the end users of your product.
- The SAVE framework (Subject-matter authority, Actionability, Value-driven, Empathy) ensures content serves a clear purpose, while the GOST framework (Goals, Organic traffic, Social shares, Time on page) helps track success.
- Each piece of content should be strategically mapped to business objectives, whether it’s driving product demos, increasing sign-ups, or nurturing leads.